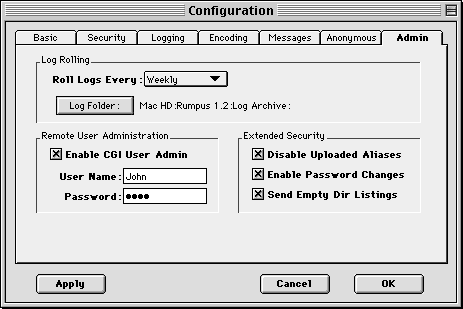
Figure 11: A configured general administration setup
The final configuration pane permits the setup of several general purpose administration options. These options make using Rumpus easier and more secure, while automating routine maintenance. Figure 11 shows a sample setup of the "Admin" Configuration tab.

Rumpus can roll logs on a daily, weekly, or monthly basis, and the old log files can be moved to any folder you choose. When logs are rolled daily, they are moved to the archive folder at midnight each day. Weekly rolling occurs at midnight each week on Saturday night. Monthly rolling archives log files at midnight on the last day of each month. Note that Rumpus must be running at the time the logs should be rolled for the files to actually be moved to the archive.
When Rumpus moves files, it appends the date the log file was rolled to the filename and stores the file in the specified log folder. You can then review the logs using a text editor, delete them, compress and archive them, or simply leave them in the log folder for permanent archival.
Disable Uploaded Aliases
To disable this possibility, Rumpus provides the option of disabling aliases that are uploaded through Rumpus FTP services. When MacBinary files are received, Rumpus checks the file to determine if it is a Finder alias. (Normal text and raw binary files can't be aliases, so MacBinary is the only way Rumpus supports to send an alias in the first place.) If the uploaded file is an alias, Rumpus simply deactivates it by changing the file type and creator codes and turning the Finder "isAlias" bit off. The file is still saved on the hard drive, but it will not be usable as an alias to any file or folder on the server.
User Password Changes
Empty Dir Listings
When a user is not allowed to see the contents of a folder, Rumpus will send a "Not Authorized" error response to the client by default. Unfortunately, many clients see this error and misinterpret it, logging the user out of the server and effectively disabling the drop box.
When checked, the "Empty Dir Listings" option makes Rumpus send an empty directory listing, instead of an error code, to the client. In this way, the contents of the directory are still hidden from users, but no error is generated. The FTP client can then complete the login process and permit users to upload files as needed. If you are implementing a drop box, or simply want to send blank directory listings instead of returning a "Not Authorized" error response, be sure to check this option.
Copyright © 1997-9 Maxum Development Corporation
http://www.maxum.com/